LinkedIn, a business and employment-oriented social networking website contain personal information of more than 500 million users from around the world making it a jackpot for cybercriminals and those looking for identity theft.
Also, since LinkedIn’s data breach of 117 million users and then its sale on the dark web has helped malicious elements compromise websites and other social media accounts using leaked credentials. OurMine is a recent example of a hacking group using leaked passwords of LinkedIn users to hack their accounts on other sites.
Recently, a new phishing scam has been detected in which Premium LinkedIn accounts are being used to trick users into giving away their login credentials and phone numbers in the hands of cybercriminals.
The scam was discovered by Malwarebytes‘ lead malware intelligence analyst Jérôme Segura who noticed that unsuspecting users have been receiving phishing links in private message and InMail hiding behind URL shortener ow.ly and gdk.mx a free hosting provider.
The message comes with following content:
“I have just shared a document with you using GoogleDoc Drive, View shared document http://ow.ly/[].”
Upon clicking the link, users are taken on a compromised website hosting a Gmail phishing page that asks them to log in with their Gmail id and passwords. It further asks for a phone number, and secondary email then displays a decoy Wells Fargo document hosted on Google Docs. But Yahoo and AOL users are also targeted in this scam since it asks for respective users to log in with their username and password, Segura added.
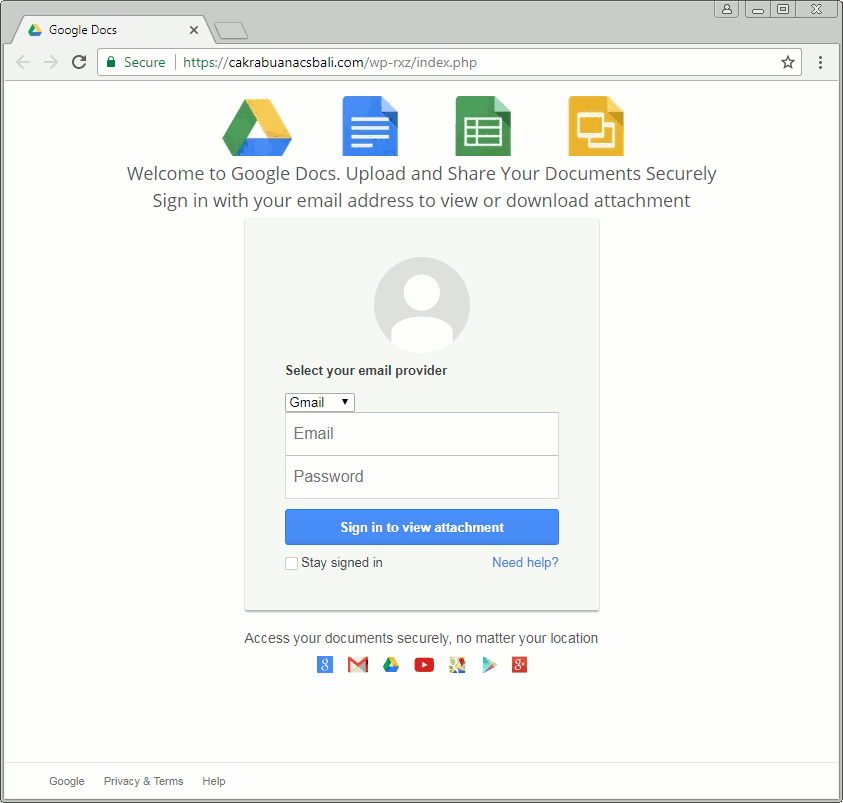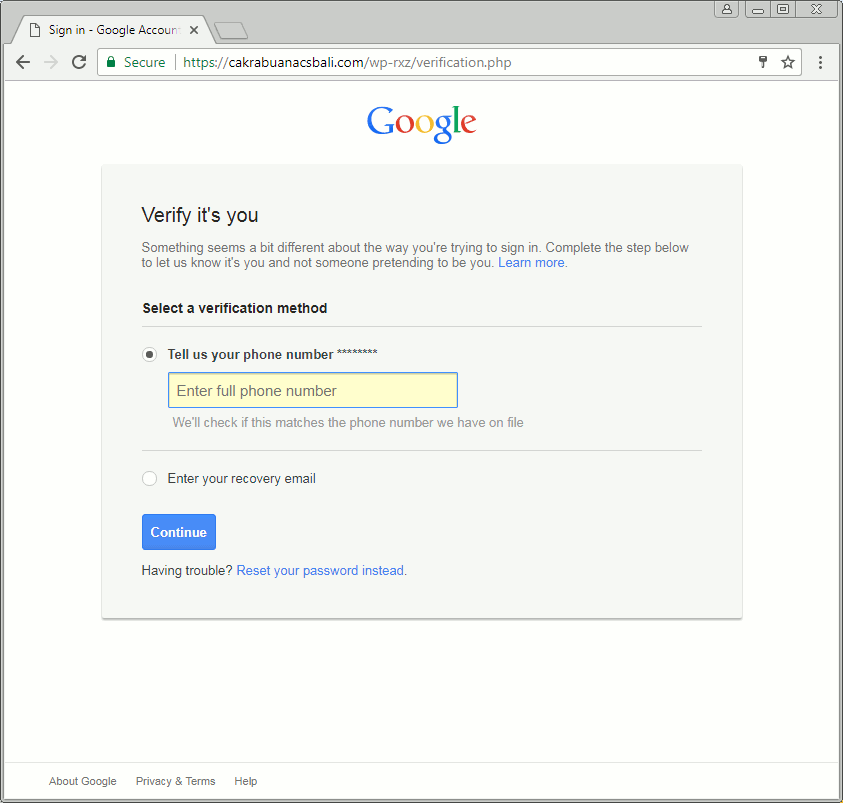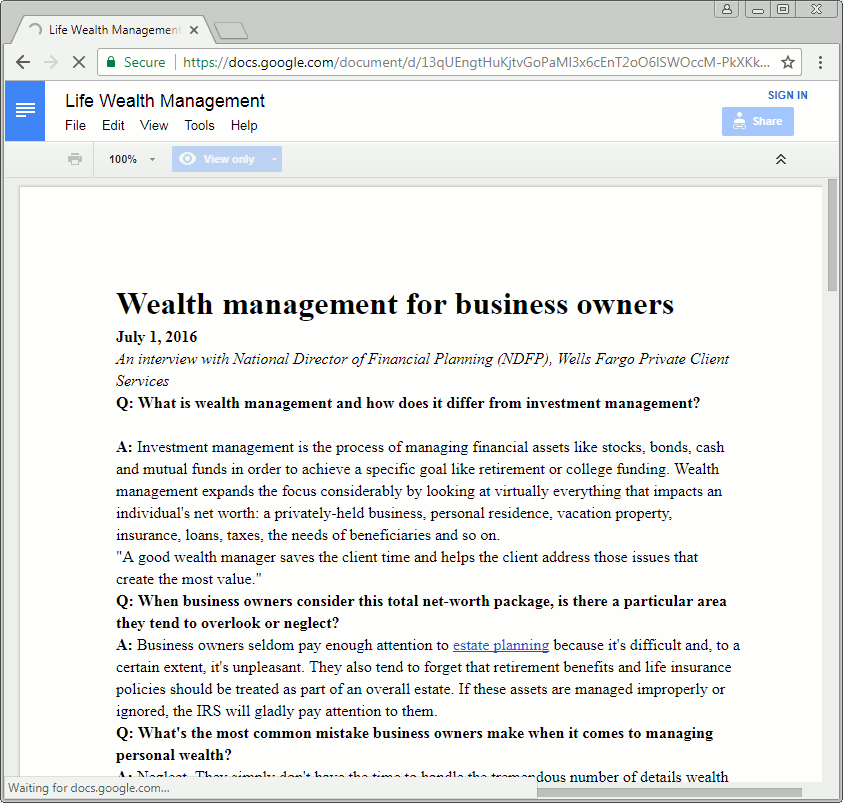
“The fraudulent message includes a reference to a shared document and a link that redirects to a phishing site for Gmail and other email providers which require potential victims to log in,” Segura explained.
“Those who proceed will have their username, password, and phone number stolen but won’t realize they were duped right away. Indeed, this phishing scam ends on a tricky note with a decoy document on wealth management from Wells Fargo.”
Furthermore, cybercriminals are also using LinkedIn InMail feature which allows Premium users to send direct messages to others even if they are not connected. Currently, it is unknown how many Premium accounts are being used to spread this scam.
Here is an example phish message sent to InMail feature:
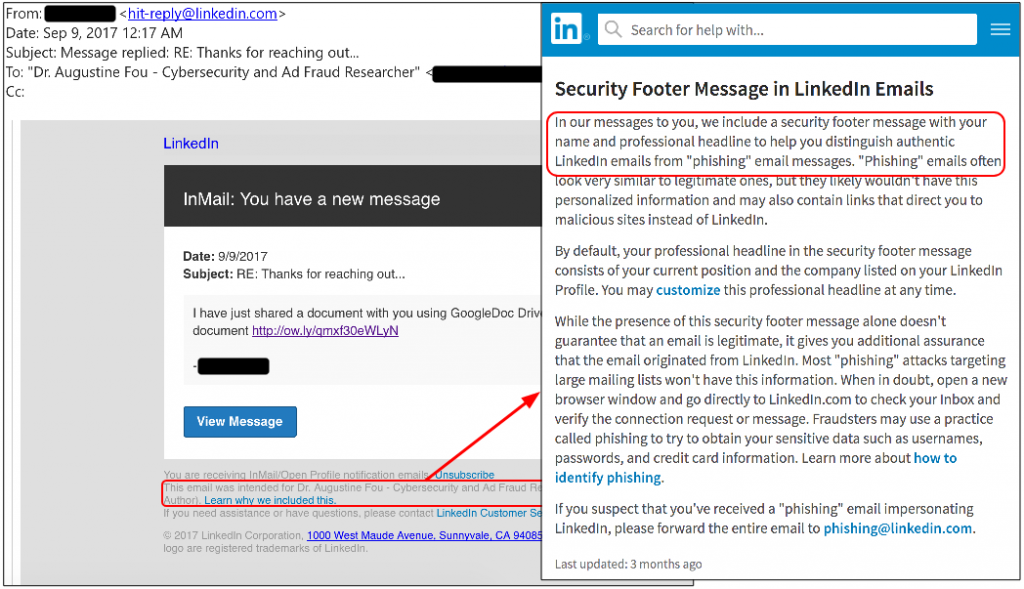
“This kind of attack via social media is not new – we have seen hacked Skype, or Facebook accounts send spam – but it reminds us of how much more difficult it is to block malicious activity when it comes from long-standing and trusted user accounts, not to mention work acquaintances or relatives. This also makes such attacks more credible to potential victims and can lead to a snowball effect when victims become purveyors of phishing links themselves,” Segura wrote.
This is not the first time when cybercriminals have used LinkedIn for phishing attacks. In November 2016, a scam used Dropbox as bait to not only steal LinkedIn login credentials but also aimed at financial details, driving license and passport copy for identity theft.
LinkedIn and other Internet users are advised not to open messages or emails from an unknown sender, never click or download attachments from an email whose sender is not known to them. Here are 5 tips to protect yourself from phishing scams. Stay safe online.